| Disclaimer: ADFS and Azure AD are products offered
by Microsoft Corporation. The configuration steps shown
here related to ADFS and Azure AD are valid at the time of writing and can be referred to as a guideline.
These configuration steps on ADFS and Azure AD can change over
time. Please refer to the latest documentation provided by the vendor for more up to
date information. |
Achieving Single Sign-On behaviour
When using ADFS for Windows 2016 or Azure Active Directory as the Open
Identity Providers it is possible to achieve Single Sign On behaviour for Aurena
Default Client, Aurena B2B Client and IFS Enterprise Explorer. For IFS Touch Apps
Single Sign On behaviour is not available.
Contents
Single sign on with ADFS for Windows 2016
A user who is logged into the Active Directory domain where AD FS service is
available will be able to login to the IFS Applications (Aurena Default client,
Aurena B2B client and Ifs Enterprise Explorer) without being prompted for user
name and password. ADFS for Winows 2016 uses Windows Integrated Authentication
(WIA) to provide SSO behaviour.
Depending on how the AD FS server is installed following
configurations might be necessary to get SSO working for domain logins:
Configurations on ADFS Server:
- Login to the Windows 2016 server where AD FS service is installed.
Launch AD FS management console (Control Panel\All Control Panel
Items\Administrative Tools\Ad FS Management)
- Expand "Service > Authentication Methods". Click "Edit" next to "Primary
Authentication Methods".
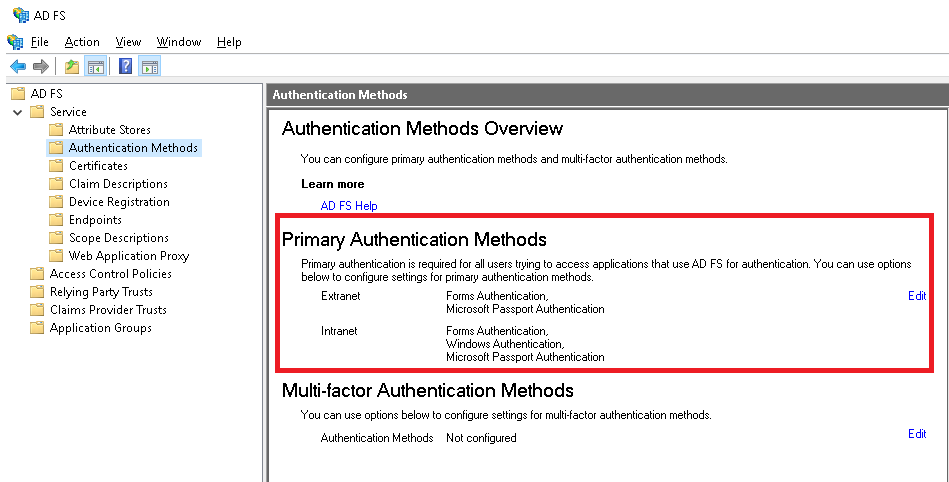
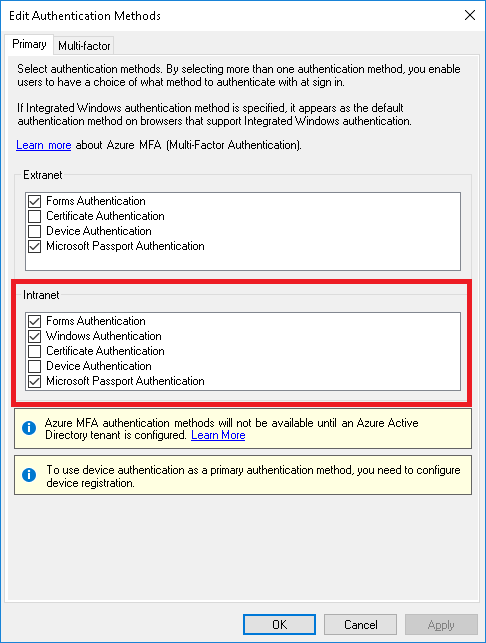
- Make sure that for "Intranet" both "Forms Authentication" and "Windows
Authentication" check boxes are ticked.
- As stated above ADFS provides SSO functionality using Windows
Integrated Authentication (WIA). WIA is enabled based on the User Agent of
the client application. If the User Agent used by the client application is
defined in the ADFS Property WIASupportedUserAgents then SSO is possible. In
order to enable WIA for IFS Enterprise Explorer, User Agent "Mozilla/4.0"
needs to be added to this property. Also if you open up Aurena Web Client
and Aurena B2B Client in Edge browser or Chrome browser the user agents
"=~Windows\s*NT,*Edge" and "Chrome" must be added to the list of allowed User Agents.
- Here is how to include the above values to WIASupportedUserAgents.
Open a Power Shell window as the administrator and type the following
command. Once the command is executed go to Windows Services and restart the
Active Directory Federation Services service.
Set-AdfsProperties -WIASupportedUserAgents
((Get-ADFSProperties | Select -ExpandProperty WIASupportedUserAgents) +
"Mozilla/4.0" + "=~Windows*NT,*Edge" + "Chrome")
- It might also be necessary to turn the AD FS property
ExtendedProtectionTokenCheck to "none".
Here also it is necessary to restart the Active Directory Federation
Services after changing this parameter.
Set-AdfsProperties -ExtendedProtectionTokenCheck none
Configurations on client workstations
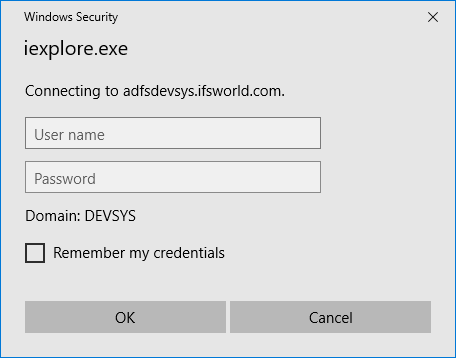
- Still in some situations (i.e: if the URL used by the ADFS Service is
different from domain URL) you will get the following Windows Security dialog
when you try to access IFS Aurena Default Client, Aurena B2B Client or IFS
Enterprise Explorer.
Windows security dialog when Internet Explorer or
Edge browser is used:
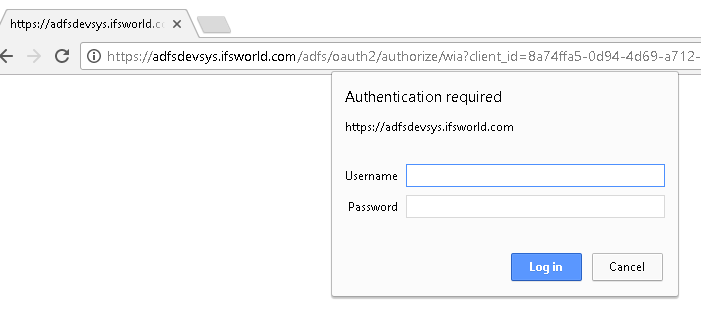
Security dialog when Chrome browser is used:
- To get rid of the Windows security dialog you have to white list the URL
used by the ADFS server and/or the Application server.
- For Chrome browser: launch the Chrome.exe with the start up parameter
--auth-server-whitelist
and provide a list of the URLs that
needs to be white listed.
E.g: chrome.exe
--auth-server-whitelist="*ifsworld.com"
- For Internet Explorer and Edge browsers: access "Internet
Options" (at Start Menu type Internet Options), select "Security" tab, select
"Local intranet" and press "Sites". Select "Advanced". In the dialog box
provided add the URL that you want to white list.
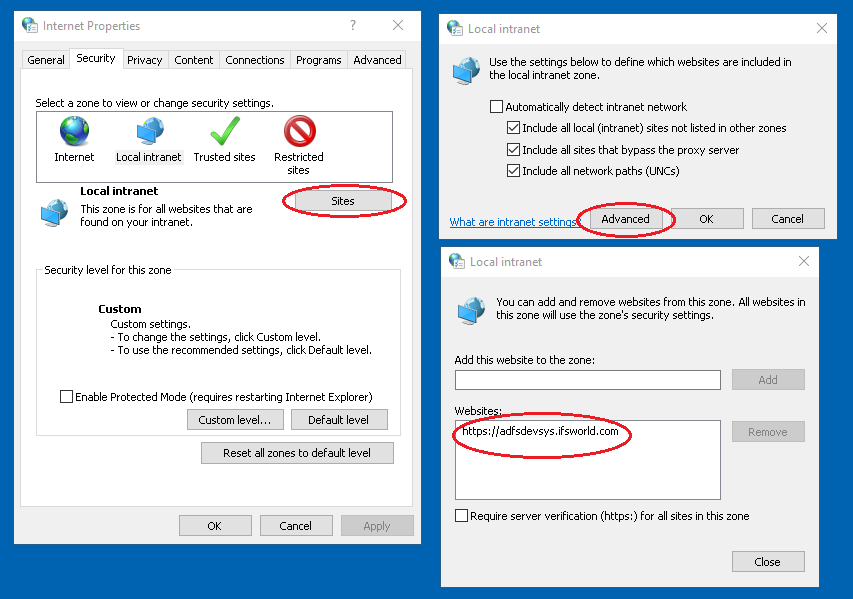
- In installations where the IFS Applications middleware server is
configured with a
Custom Client Access URL (this configuration is used when an
external
load balancer or a proxy server is used) that URL must also be white listed as
shown above for SSO to work properly.
- When you get the Windows security dialog above if you click
"Remember my credentials" check box and enter your credetials they will
be cached in Windows. These will be used on subsequent logins and you
will not be able to see this dialog again. In case you want to get this
dialog back so that you can login as a different user you have to follow
the following procedure:
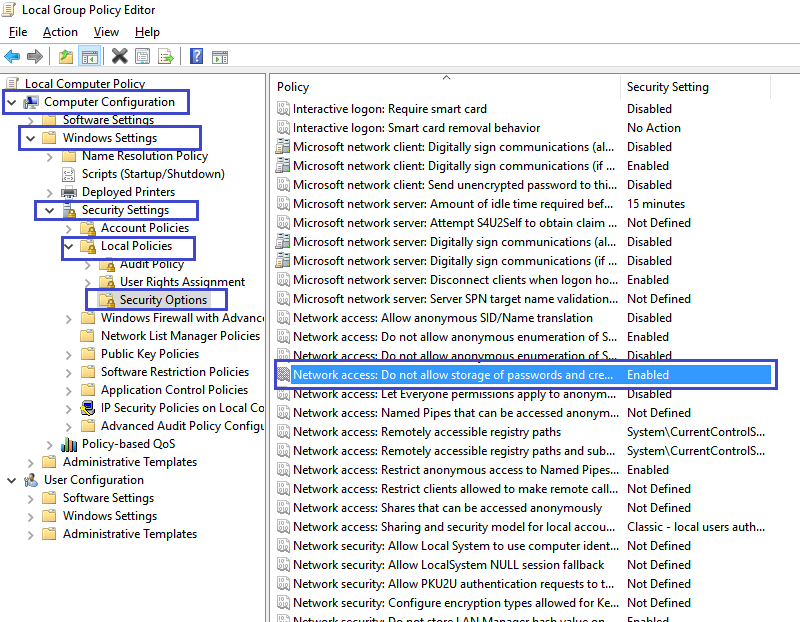
- Go to start menu and type "Group policy". Select "Edit group
policy" and "Local Group Policy Editor" will open.
- Select "Computer configuration > Windows Settings >
Security settings > Local Policies> Security options.
- Select "Network Access: Do not allow storage of passwords
and credentials for network authentication" and "Enable" it.
SSO for Aurena Web Client and Aurena B2B client
If the ADFS server configurations and browser configurations are done as
described above when you try to access Aurena Web or Aurena B2B client you will
not be prompted with a login dialog but will get logged into the application
using your domain credentials.
SSO for IFS Enterprise Explorer
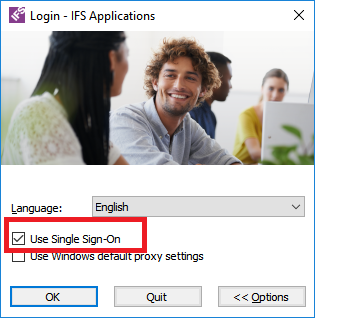
- When launching the application keep pressing the <SHIFT> key. You will
be presented with the below shown dialog. Tick the "Single Sign-on Option"
and press "OK"
- You will be logged into the application using your domain credentials.
- The setting will be saved in the user settings and will be valid for
all the subsequent logins. Which means all the subsequent logins will happen
as SSO. If you want to change this behavior you will have to press
"SHIFT" while the application launches and get the initial dialog.
- The SSO behavior is controlled by the setting. By default it will be
disabled, You can enable it and all the IFS EE client logins will get SSO
behavior after that.
Single sign on with Azure Active Directory
If the users login to the devices (workstations where the client
are launched from) using an Azure Active Directory account or the corporate On
Premise Active Directory is integrated to Azure Active Directory (Azure AD
Connect) it is possible to achieve a Single Sign On experience for IFS Aurena Web
client, IFS Aurena B2B client and IFS Enterprise Explorer. The user has to be
available in in the same Azure AD Tenant the applications have been
registered in.
SSO for Aurena Web Client and Aurena B2B client
- The user launches the client using the IFS Application landing page
opened on Internet Explorer, Edge or Chrome
browser. The following Azure AD login dialog may appear, prompting
the user to enter the user name:
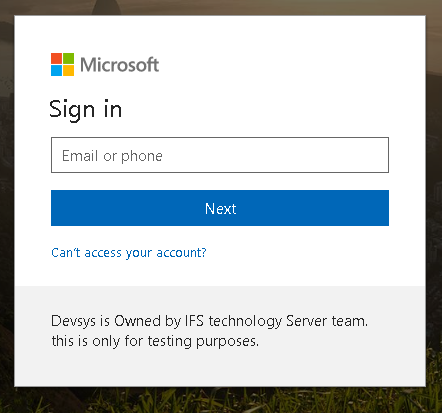
- Enter the user's corporate email address here. Alternativley you can enter
the user's userPrincipleName which was used to login to the device. (In most
cases userPrincipalName is the same as the user's corporte email address).
- Once you press "Next" you will be signed on to the application seemlessly
and you will not be prompted for a password.
SSO for IFS Enterprise Explorer
- Launch the IFS Enterpris Explorer client using the IFS Applications
landing page. While the application is opeing keep pressing the "Shift"
key. The following dialog will appear.

- Tick the tick box "Use Single Sign-On" and press OK.
- User's corporate email address will be used as the login hint and user
will be seemlessly logged in to IFS Enterprise Exlporer. No login dialog to
enter user id or password will appear.










